Refer to the topology diagram in the exhibit.
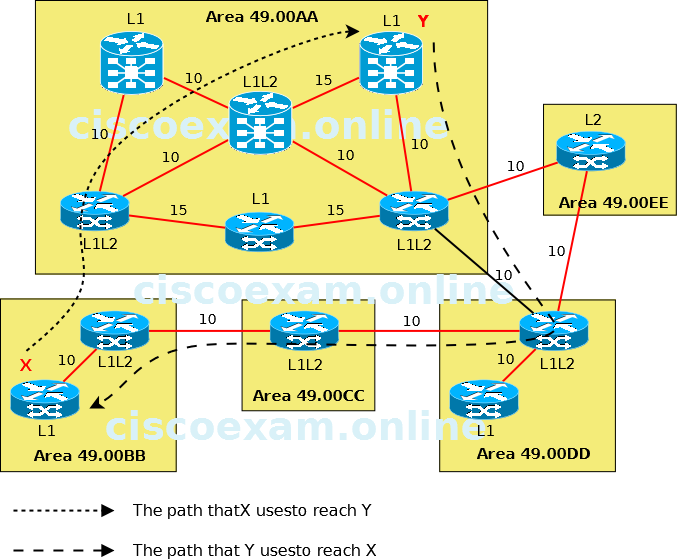
Which IS-IS feature could be implemented so that the return path for the packets from router Y in area 49.00AA to router X in area 49.00BB will use the more optimal path?
| A. |
Enable route leaking to pass Level 2 information into the Level 1 routers. | |
| B. |
Change the area 49.00AA type from a stub area to a regular area. | |
| C. |
Change the IS-IS administrative distance on router Y in area 49.00AA. | |
| D. |
Change the IS-IS metric type from narrow to wide on all IS-IS routers. |
The ISIS routing protocol allows for a twolevel hierarchy of routing information. There can be multiple Level 1 areas interconnected by a contiguous Level 2 backbone. A router can belong to Level 1, Level 2, or both. The Level 1 linkstate database contains information about that area only. The Level 2 linkstate database contains information about that level as well as each of the Level 1 areas. An L1/L2 router contains both Level 1 and Level 2 databases. It advertises information about the L1 area to which it belongs into L2. Each L1 area is essentially a stub area. Packets destined for an address that is outside of the L1 area are routed to the closest L1/L2 router to be forwarded on to the destination area. Routing to the closest L1/L2 router can lead to suboptimal routing when the shortest path to the destination is through a different L1/L2 router. Route leaking helps reduce suboptimal routing by providing a mechanism for leaking, or redistributing, L2 information into L1 areas. By having more detail about inter area routes, an L1 router is able to make a better choice with regard to which L1/L2 router to forward the packet.